Russia’s Bold Sabotage Campaign Escalates: FSB’s Cyber Onslaught Targets Polish Energy Infrastructure
Executive Summary
In the waning days of 2025, a series of meticulously orchestrated cyber intrusions upon Poland’s energy sector underscored the intensifying audacity of Russia’s hybrid warfare stratagems.
Attributed with considerable certitude to the Federal Security Service’s clandestine operatives, these assaults imperiled critical infrastructure, nearly precipitating a cataclysmic blackout amid plummeting temperatures.
FAF comprehensive analysis divuges Kremlin’s evolving tactics of subversion but also portends broader ramifications for European security architecture, necessitating a reevaluation of collective defense postures and resilience mechanisms.
Introduction
The geopolitical landscape of Eastern Europe has long been fraught with tensions emanating from Moscow’s revisionist ambitions, yet the December 29, 2025, cyber offensives against Polish energy installations represent a paradigm shift in the modality of confrontation.
These incursions, targeting over 30 renewable energy facilities alongside a pivotal combined heat and power plant, evince a deliberate escalation in Russia’s campaign of asymmetric aggression.
By leveraging sophisticated digital tools to disrupt vital services, the Kremlin seeks to erode the resolve of NATO’s eastern flank without invoking overt military reprisals.
This analysis delves into the historical antecedents, contemporaneous dynamics, and prospective trajectories of such operations, illuminating the intricate interplay of espionage, technology, and statecraft in the contemporary arena of international relations.
History and Current Status
The antecedents of Russia’s sabotage endeavors in Poland trace back to the post-Cold War era, wherein Moscow perceived Warsaw’s westward orientation as an existential affront to its sphere of influence.
Following the 2014 annexation of Crimea and the ensuing conflict in Donbas, Poland emerged as a linchpin in Western support for Ukraine, channeling arms and humanitarian aid while fortifying its own defenses.
This positioning rendered it a prime target for hybrid tactics, encompassing disinformation campaigns, espionage, and physical sabotage.
By 2022, incidents such as railway disruptions and arson plots had become recurrent, often linked to proxies or deniable assets affiliated with Russian intelligence apparatuses.
In the current milieu, Russia’s sabotage apparatus has matured into a multifaceted enterprise, integrating cyber capabilities with traditional covert operations.
The Federal Security Service, or FSB, particularly its Center 16 unit, has been implicated in a litany of intrusions across Europe, from energy sector reconnaissance to disruptive malware deployments.
Poland’s status as a NATO vanguard state amplifies its vulnerability; with a shared border proximate to Belarus—a de facto Russian satrapy—and Kaliningrad, the exclave brimming with military assets, Warsaw contends with perpetual threats.
Recent assessments indicate that Moscow orchestrates up to fifty sabotage attempts daily against Polish targets, ranging from digital incursions into hospitals and water supplies to physical detonations on infrastructure.
This sustained pressure not only strains domestic resources but also tests the cohesion of transatlantic alliances.
Key Developments
The trajectory of Russian sabotage in Poland has witnessed pivotal evolutions, commencing with low-intensity provocations and ascending to high-stakes cyber warfare.
In 2023, hackers affiliated with Moscow commandeered railway signaling systems in northwestern Poland, halting twenty trains and sowing chaos in logistics chains integral to Ukrainian resupply efforts.
The ensuing year saw arson attempts on warehouses storing military materiel, alongside drone incursions that violated sovereign airspace, prompting NATO scrambles.
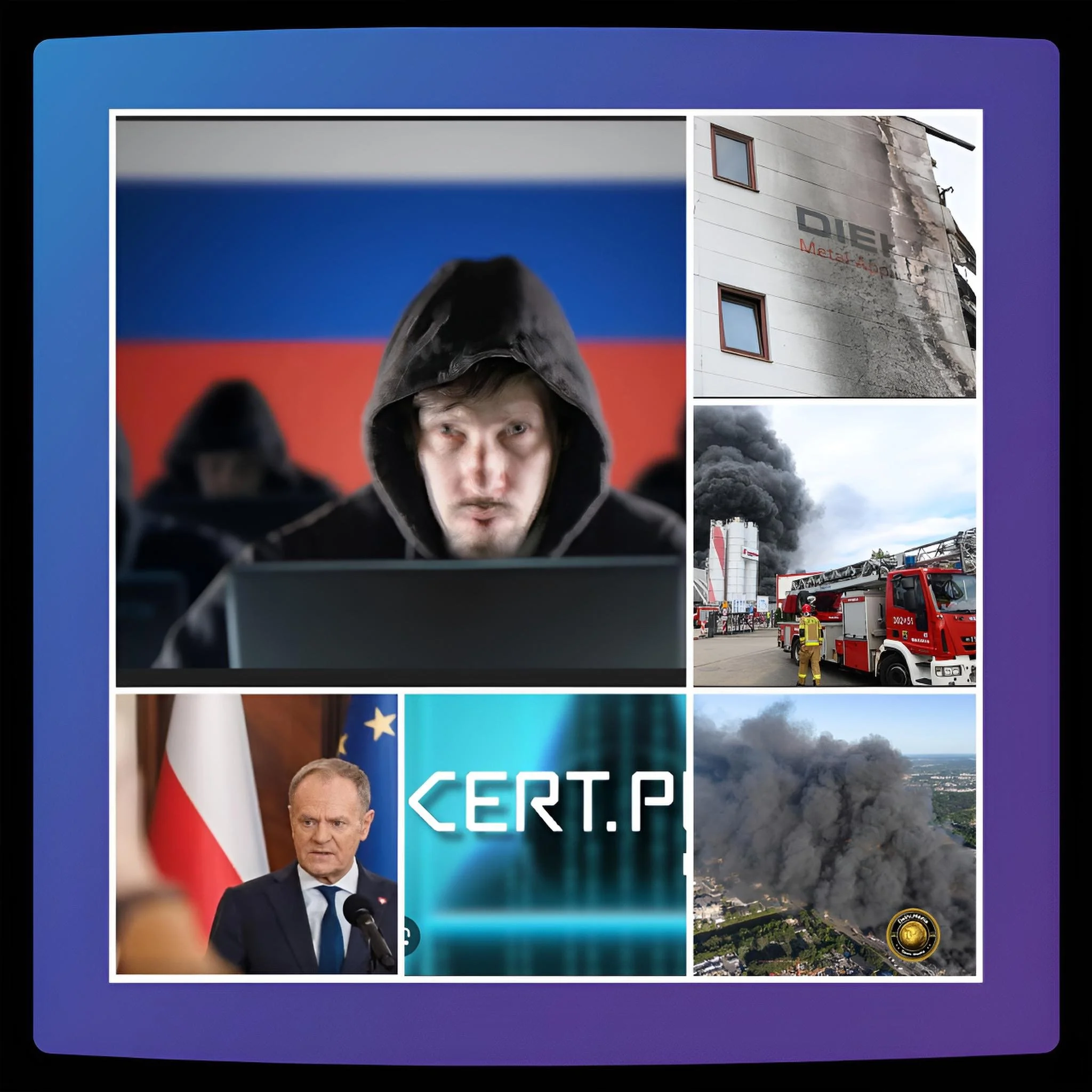
These acts, while disruptive, paled in comparison to the December 2025 assaults, which exploited vulnerabilities in FortiGate perimeter devices to deploy destructive malware such as DynoWiper.
This malware, designed to irreparably corrupt data, targeted wind and photovoltaic farms, a manufacturing entity, and a heat plant servicing nearly 500,000 residents.
The synchronization of these attacks amid severe winter conditions—temperatures dipping below freezing—amplified their potential lethality, aiming to induce widespread panic and infrastructural collapse.
Polish CERT’s attribution to the FSB’s Berserk Bear cluster, also known as Dragonfly or Static Tundra, draws from forensic evidence linking the operation to prior espionage campaigns documented by the FBI in August 2025.
Divergent attributions by entities like ESET to the GRU’s Sandworm underscore the opacity of Russian intelligence silos, yet consensus prevails on state sponsorship.
Latest Facts and Concerns
Empirical data from the incident reveals a near-catastrophic outcome: the assaults compromised communications at over thirty sites, with the CHP plant’s data obliteration narrowly averted by redundant safeguards.
Polish authorities thwarted a blackout that could have affected millions, but residual disruptions persisted, highlighting systemic frailties in renewable energy grids.
Concerns abound regarding the escalation’s implications; Russia’s pivot to destructive cyber operations signals a departure from mere reconnaissance, potentially presaging similar strikes on Baltic undersea cables or Scandinavian power networks.
Broader anxieties encompass the hybridization of warfare, wherein cyber tools complement physical sabotage, such as the recent Balticconnector pipeline rupture attributed to Russian-linked vessels.
2025 alone, the spillover into NATO territory erodes deterrence thresholds.
Economic repercussions loom large: Poland’s energy sector, pivotal to its GDP, faces heightened insurance premiums and investment deterrence, while societal trust in governmental resilience wanes amid disinformation torrents.
Cause-and-Effect Analysis
The causal nexus of these sabotage acts resides in Russia’s strategic imperatives to undermine Western unity and reclaim influence over former satellites.
The invasion of Ukraine in 2022 catalyzed this campaign, as Poland’s staunch advocacy for Kyiv—manifest in arms transfers exceeding $3 billion—positioned it as a bulwark against Muscovite expansionism.
Effects cascade multifariously: domestically, such intrusions exacerbate energy insecurity, with potential GDP contractions of up to 2% in affected regions due to outages.
Geopolitically, they probe NATO’s Article 5 commitments, fostering hesitation among allies wary of escalation.
A ripple effect materializes in allied responses; heightened vigilance in Estonia and Lithuania, for instance, has spurred joint naval patrols, while Germany’s military counterintelligence reports a surge in hybrid threats.
Conversely, Russia’s internal calculus—bolstered by evading sanctions through parallel imports—emboldens further aggression, perpetuating a cycle wherein perceived Western weakness invites bolder incursions.
Future Steps
To mitigate this burgeoning menace, a multifaceted strategy is imperative. Poland should expedite the fortification of critical infrastructure, mandating multi-factor authentication and zero-trust architectures across energy networks.
Collaborative endeavors with NATO, such as the Baltic Sentry mission, must expand to encompass cyber domain exercises and intelligence fusion centers.
The European Union ought to harmonize sanctions regimes, targeting FSB enablers and cryptocurrency channels facilitating operative payments.
Diplomatically, engaging neutral stakeholders to isolate Russia economically could diminish its operational bandwidth.
Investment in resilient technologies—such as decentralized grids and AI-driven anomaly detection—will prove pivotal. Ultimately, a unified transatlantic posture, including enhanced U.S. commitments under the Biden administration’s successor, is essential to deter escalation.
Conclusion
The FSB-orchestrated hacks on Polish energy plants epitomize Russia’s audacious reconfiguration of conflict paradigms, blending cyber prowess with geopolitical brinkmanship to fracture European solidarity.
As hybrid warfare proliferates, the imperative for robust countermeasures intensifies, lest unchecked aggression precipitate broader conflagration.
In navigating this precarious epoch, the West must reaffirm its collective resolve, transforming vulnerability into fortified deterrence.